Updated on GitHub 4 months ago (see history)
How to configure Borg client on macOS using command-line
Requirements
- Borg server (self-hosted or cloud-based such as BorgBase or rsync.net)
- Computer running macOS Catalina or Big Sur
Caveats
- When copy/pasting commands that start with
$, strip out$as this character is not part of the command - When copy/pasting commands that start with
cat << "EOF", select all lines at once (fromcat << "EOF"toEOFinclusively) as they are part of the same (single) command
Setup guide
Heads-up: steps 1 to 4 are only required if using BorgBase or rsync.net (don’t forget to enable 2FA).
Step 1: create borg SSH key pair (if using BorgBase or rsync.net)
When asked for file in which to save key, enter borg.
When asked for passphrase, use output from openssl rand -base64 24 (and store passphrase in password manager).
Use borg.pub public key when configuring Borg server.
Step 2: create borg-append-only SSH key pair (if using BorgBase or rsync.net)
When asked for file in which to save key, enter borg-append-only.
When asked for passphrase, leave field empty for no passphrase (this public key will be used for append-only operations).
Use borg-append-only.pub public key when configuring Borg server.
Step 3: configure SSH keys and create repo (if using BorgBase)
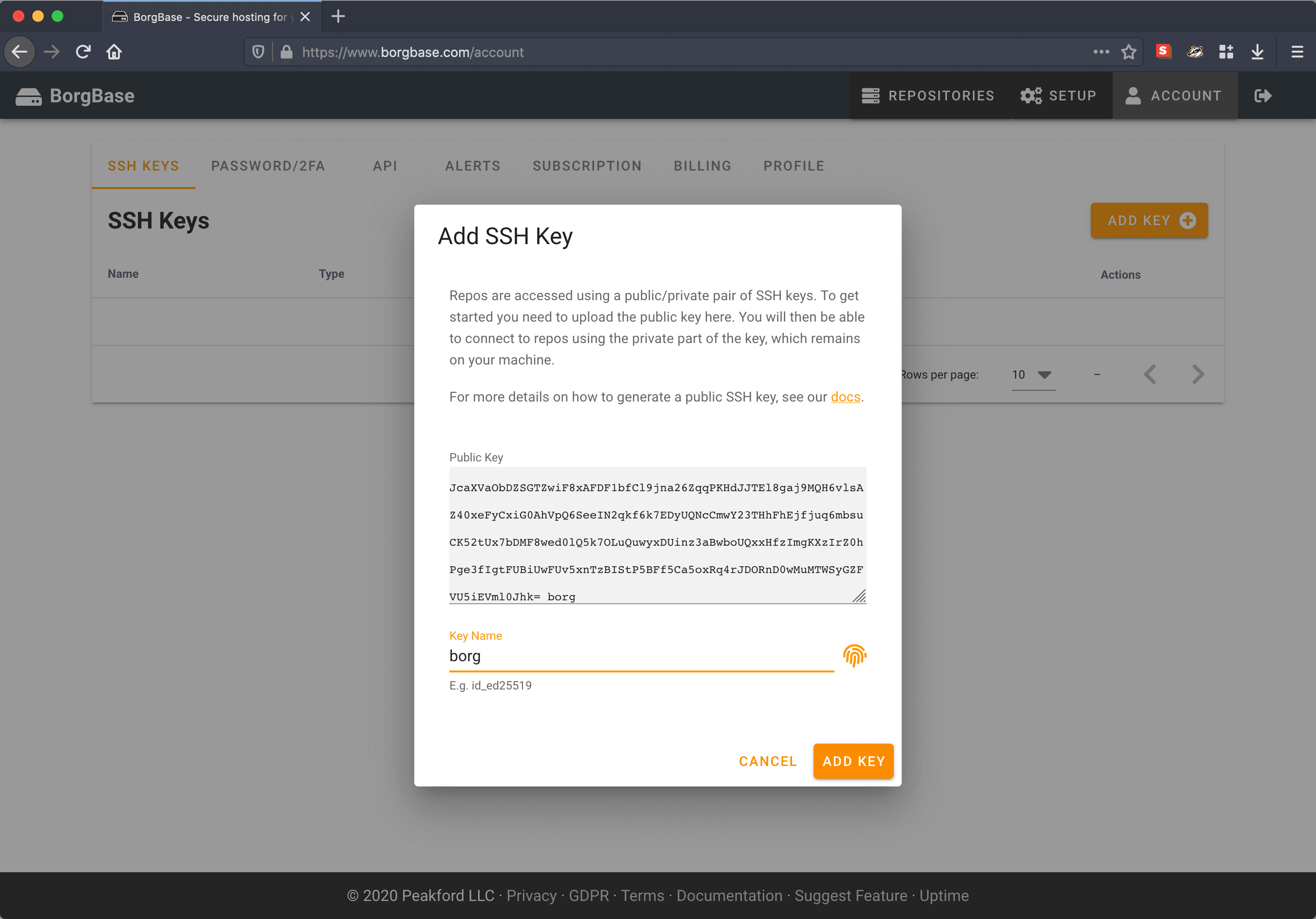
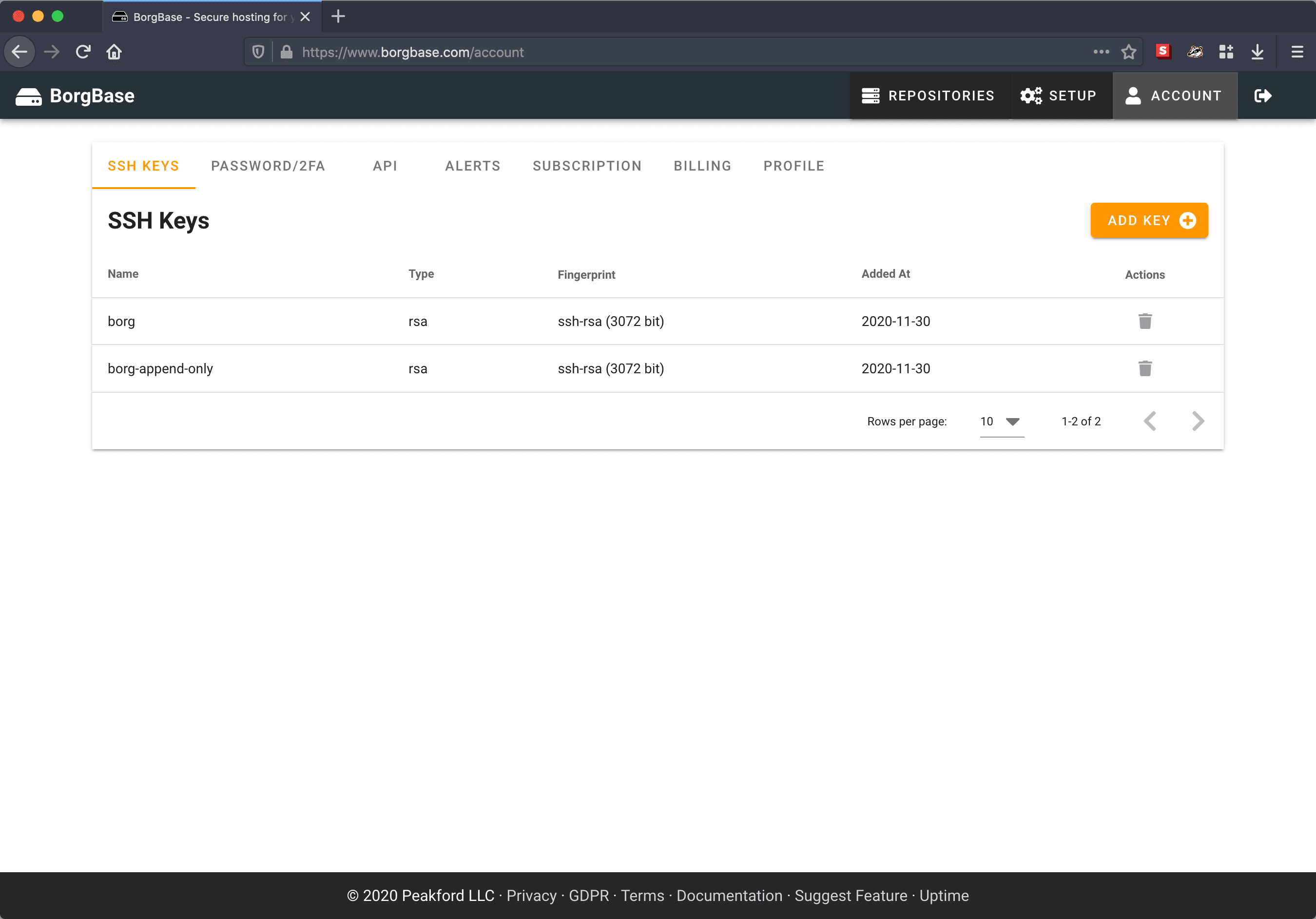
Configure SSH keys
Go to SSH Keys and add borg.pub and borg-append-only.pub keys.
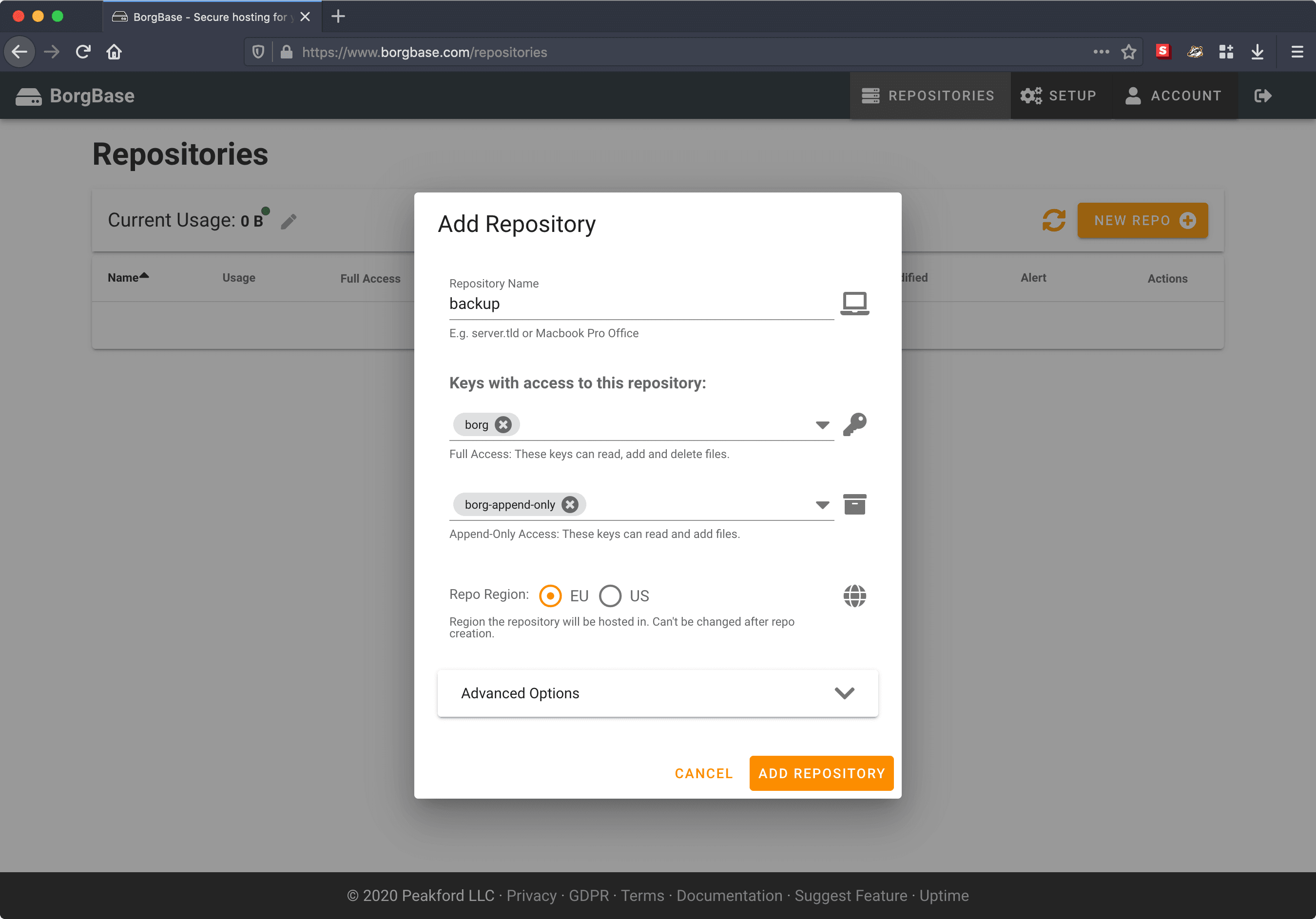
Create repo
Go to Repositories and add repository.
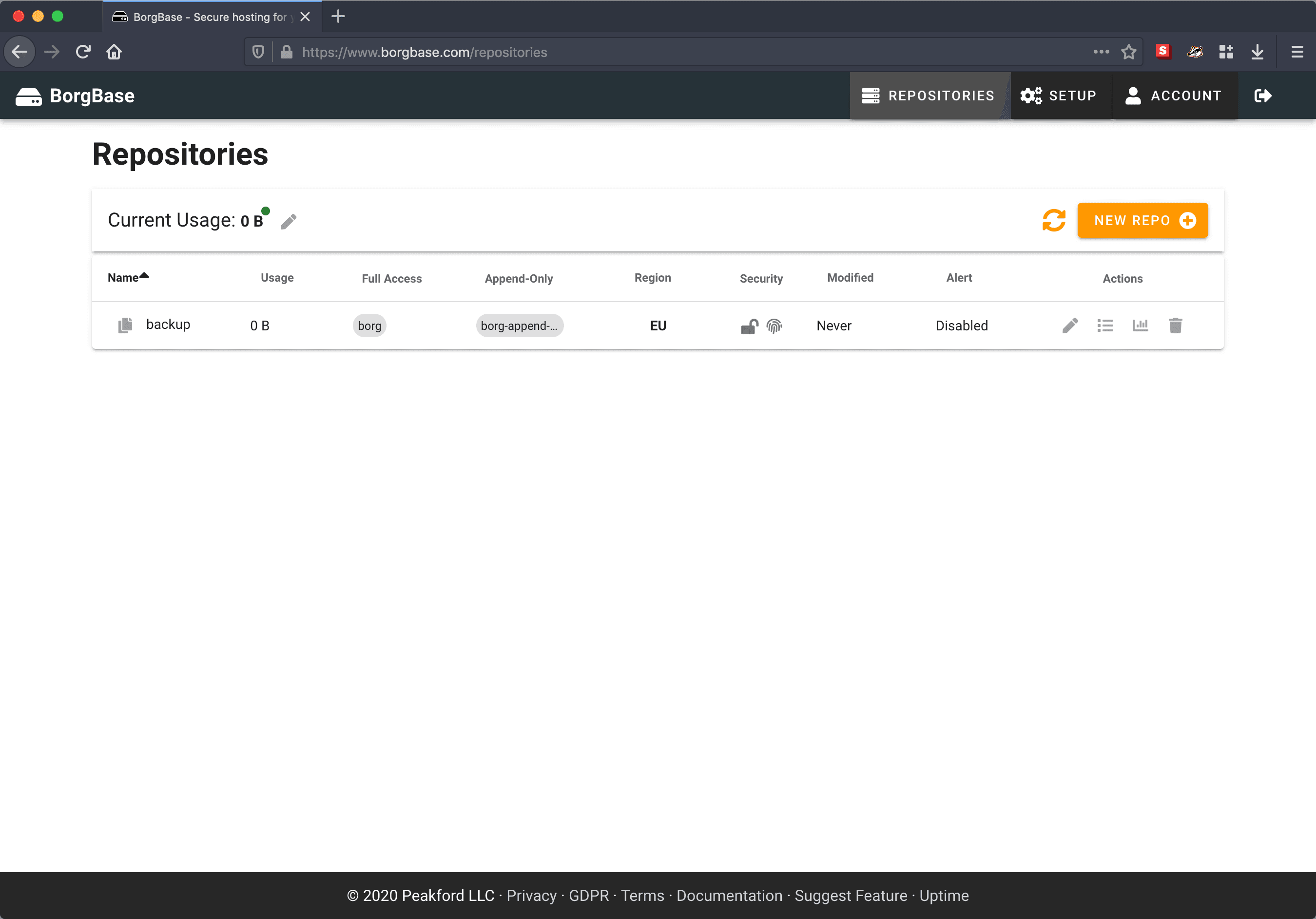
Step 4: generate and upload authorized_keys file (if using rsync.net)
Set environment variables
Generate authorized_keys file
Upload authorized_keys file
Step 5: install Homebrew
Step 6: disable Homebrew analytics
Step 7: install FUSE for macOS, Borg and Borg Wrapper
Heads-up: when installing Borg using
brew install borgbackup, one can no longer runbrew mount(see issue) so I created a tap that includes a patched version of borgbackup called borgbackup-fuse.
Heads-up: if
brew install --cask macfusefails, trybrew cask install macfuse(see issue).
Step 8: configure Borg
Generate Borg passphrase using openssl and add passphrase to “Keychain Access”
Initialize Borg repo
Heads-up: replace
borg@185.112.147.115:backupwith self-hosted or cloud-based repo.
Back up ~/.config/borg and ~/Library/Keychains folders (learn how here)
Heads-up: both key (stored in
~/.config/borg) and passphrase (stored in~/Library/Keychains) are required to decrypt backup.
Step 9: set environment variables
Heads-up: replace
borg@185.112.147.115:backupwith self-hosted or cloud-based repo and set backup name.
Step 10: create /usr/local/bin/borg-backup.sh script
Step 11: edit /usr/local/bin/borg-backup.sh script
Step 12: create /usr/local/bin/borg-list.sh script
Step 13: create /usr/local/bin/borg-check.sh script
Step 14: create /usr/local/bin/borg-restore.sh script
Step 15: create /usr/local/bin/borg-prune.sh script
Step 16: create /usr/local/var/log directory
Step 17: run “Borg Wrapper”
Heads-up: given “Borg Wrapper” is developed outside the Apple Developer Program, macOS prevents opening the app without explicit user consent (granted by clicking “Open Anyway” in “System Preferences” / “Privacy & Security”).
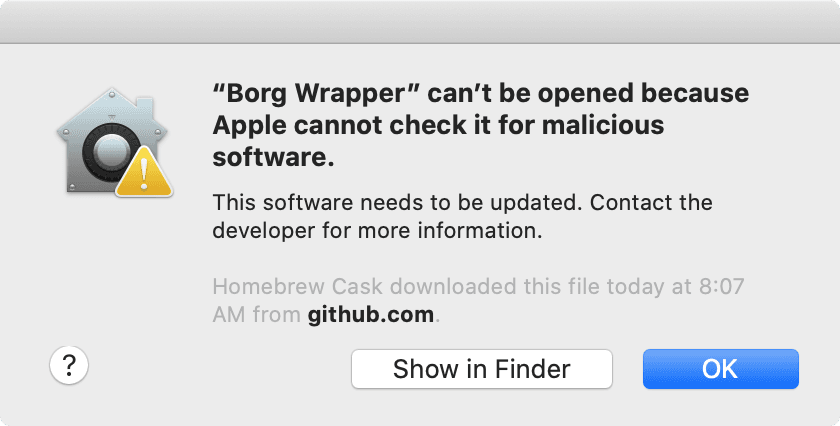
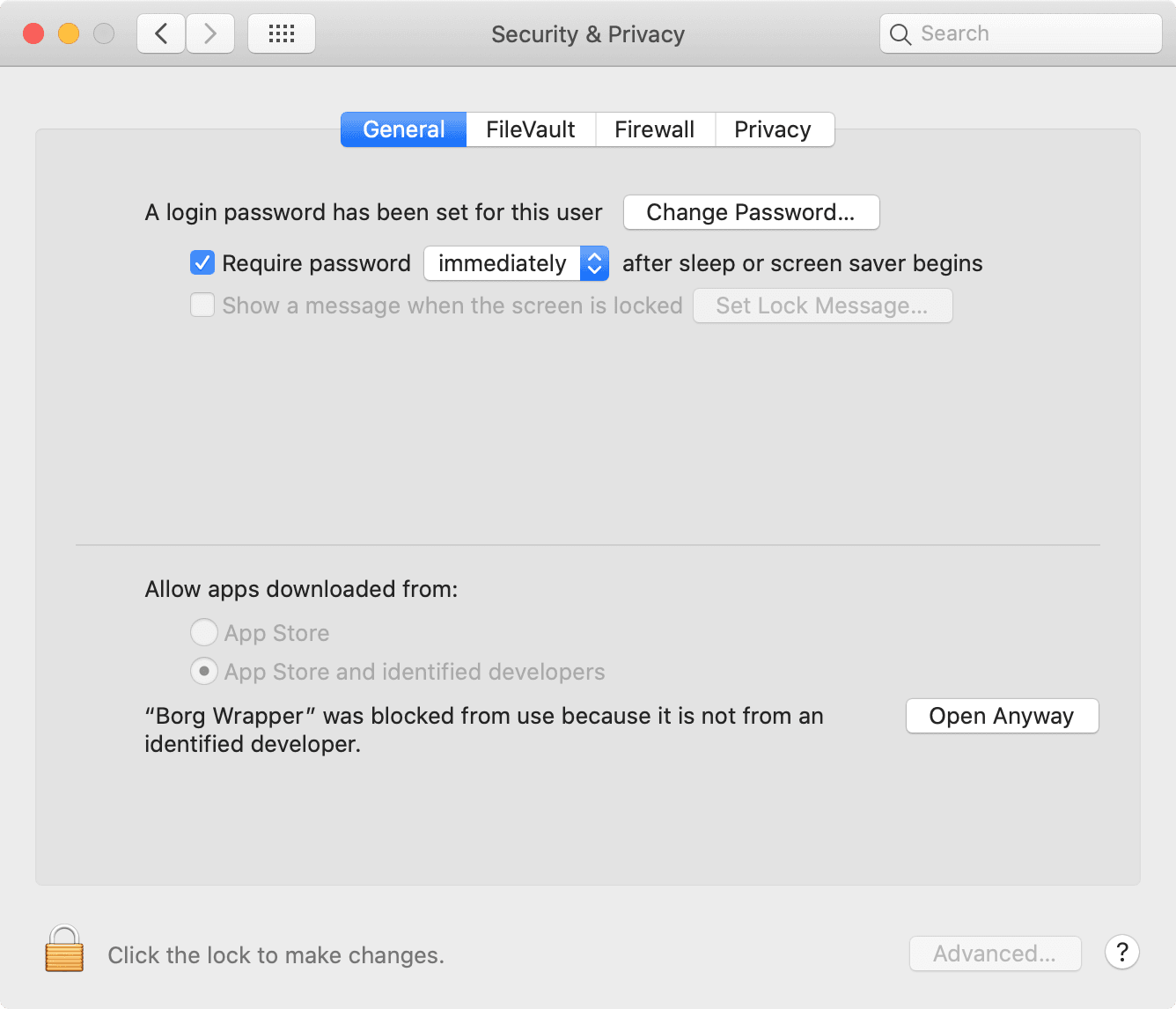
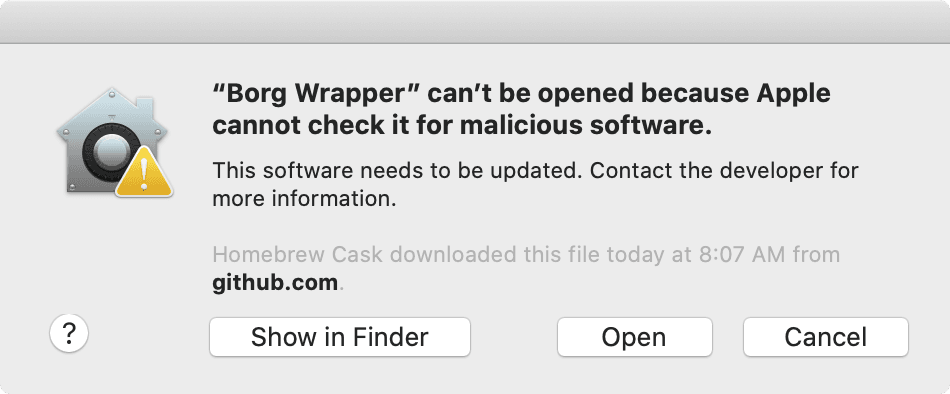
Backup completed
👍
Step 18: schedule backup every hour using launchd
👍
Usage guide
Backup
Done
👍
List
Done
👍
Check
Done
👍
Restore
Heads-up: given “FUSE for macOS” is a third-party extension, macOS prevents using the extension without explicit user consent (granted by clicking “Allow” in “System Preferences” / “Privacy & Security”).
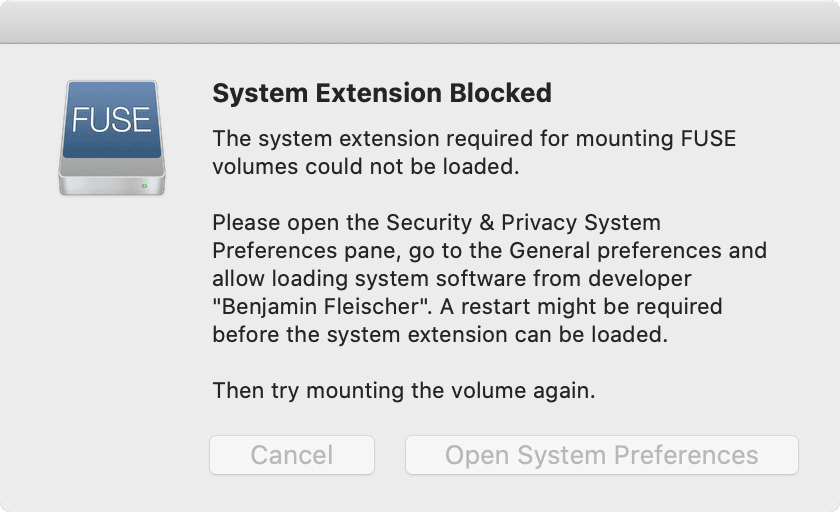
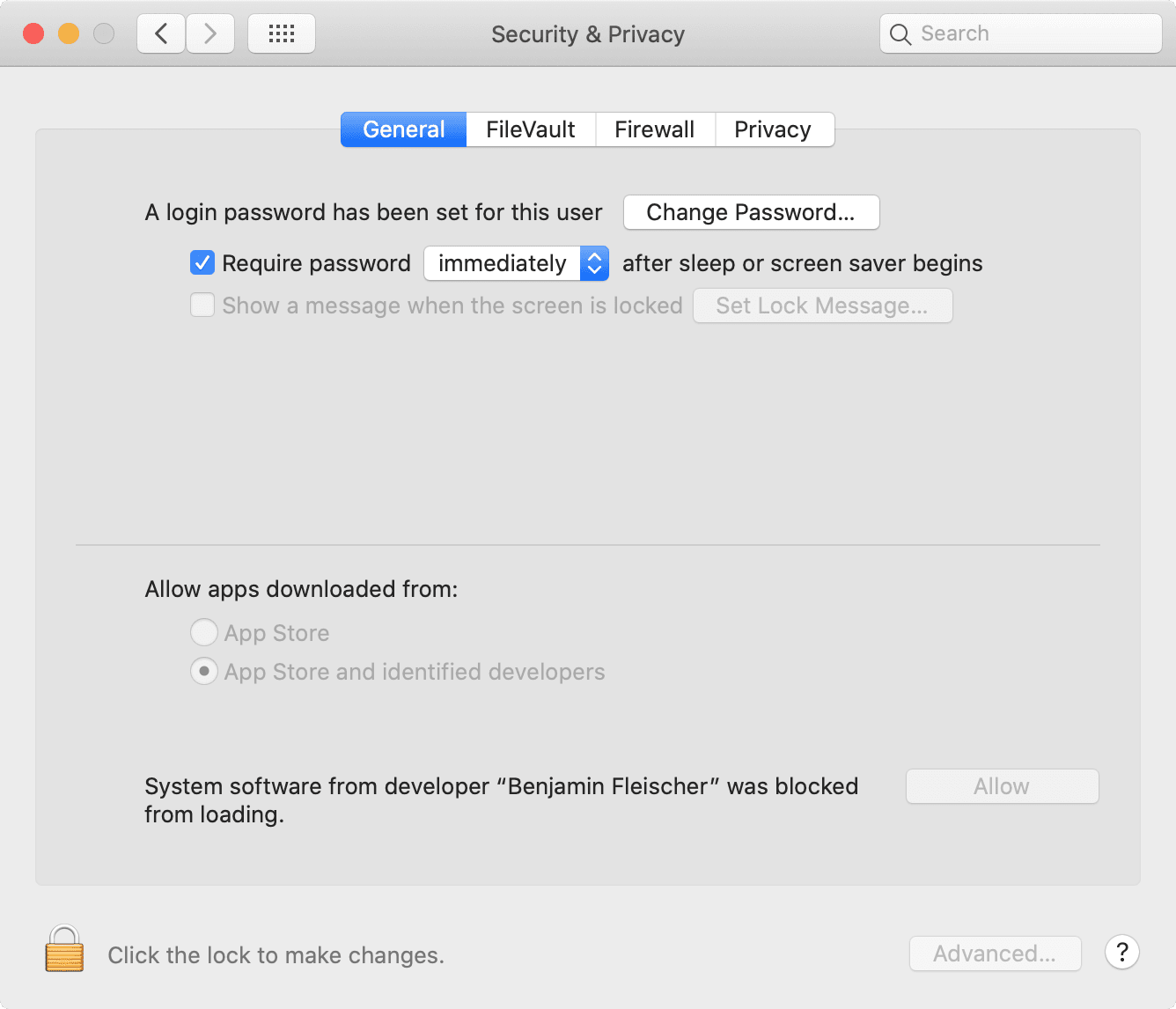
Done
👍
Prune
Done
👍